Context-Aware DSPM
Cyberhaven discovers and classifies your data, detects vulnerabilities as it flows across environments, then secures it automatically.
Why legacy DSPM isn't enough
The limitations of traditional DSPM
Traditional data security posture management tools only show you where your data sits, but fail to understand how it's used, distinguish what's truly sensitive, or stop it from leaving secure environments.
Generates false positives
Without knowing the ownership of data, whether it belongs to your company or is public data, traditional tools can't effectively determine risks.
Treats all sensitive data the same
Traditional DSPM tools provide one-size-fits-all classification, labeling everything as “sensitive” and creating noise instead of highlighting genuinely critical business data.
Lacks enforcement
Traditional DSPM shows you problems but can't act on them. When sensitive data starts moving, that’s where their protection ends.
How we're rethinking DSPM
Cyberhaven redefines DSPM
The only DSPM that combines proprietary AI, comprehensive data visibility, real-time enforcement, and GenAI guardrails.
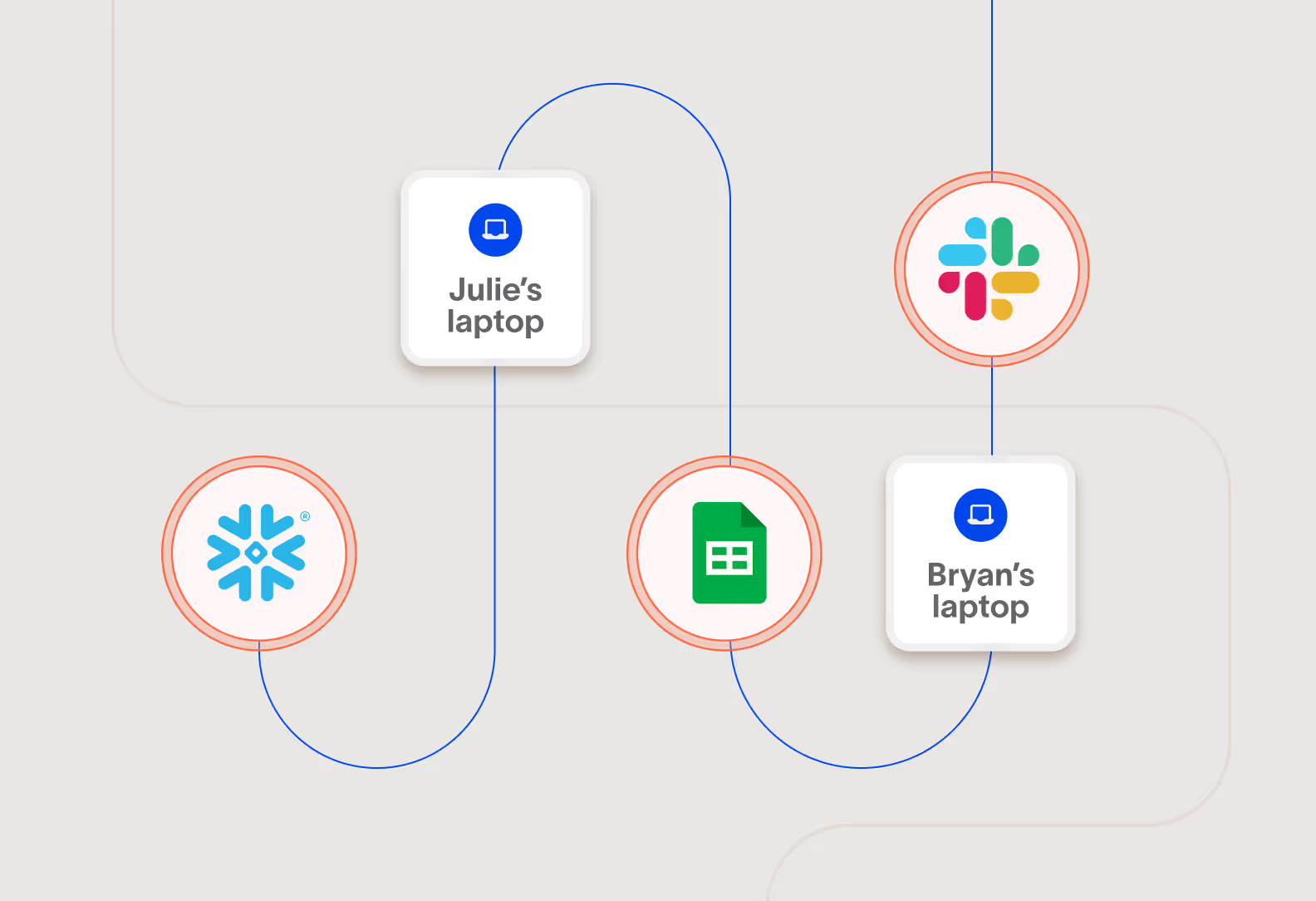
AI that sees and understands your data wherever it lives and goes
Cyberhaven’s AI discovers data residing across endpoints and the cloud, then builds a clear lineage of how it moves and changes. This comprehensive visibility helps you minimize data sprawl and achieve a security posture quickly.
Go beyond visibility to protect data
DSPM gives you the map, but DLP builds the guardrails. While existing data security tools force you to pick between visibility or enforcement, Cyberhaven delivers both. We provide comprehensive data discovery and classification alongside real-time controls to monitor, alert, and block sensitive data from leaving controlled environments.
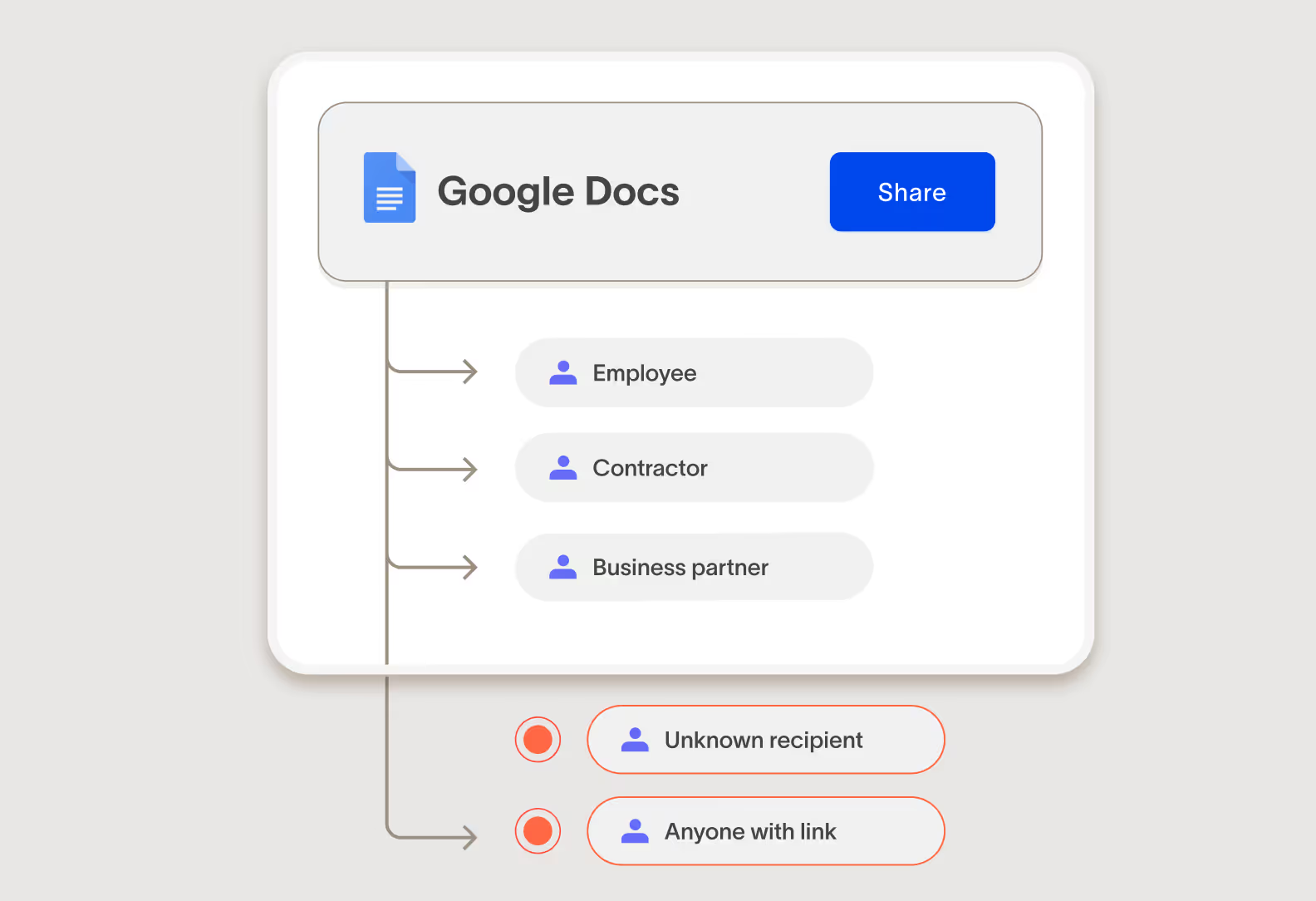
Privacy and compliance
Create a comprehensive registry of regulated data to support audit readiness. Automatically monitor and control non-compliant access, storage, and sprawl of PII to strengthen your compliance posture across every stage of the data lifecycle.
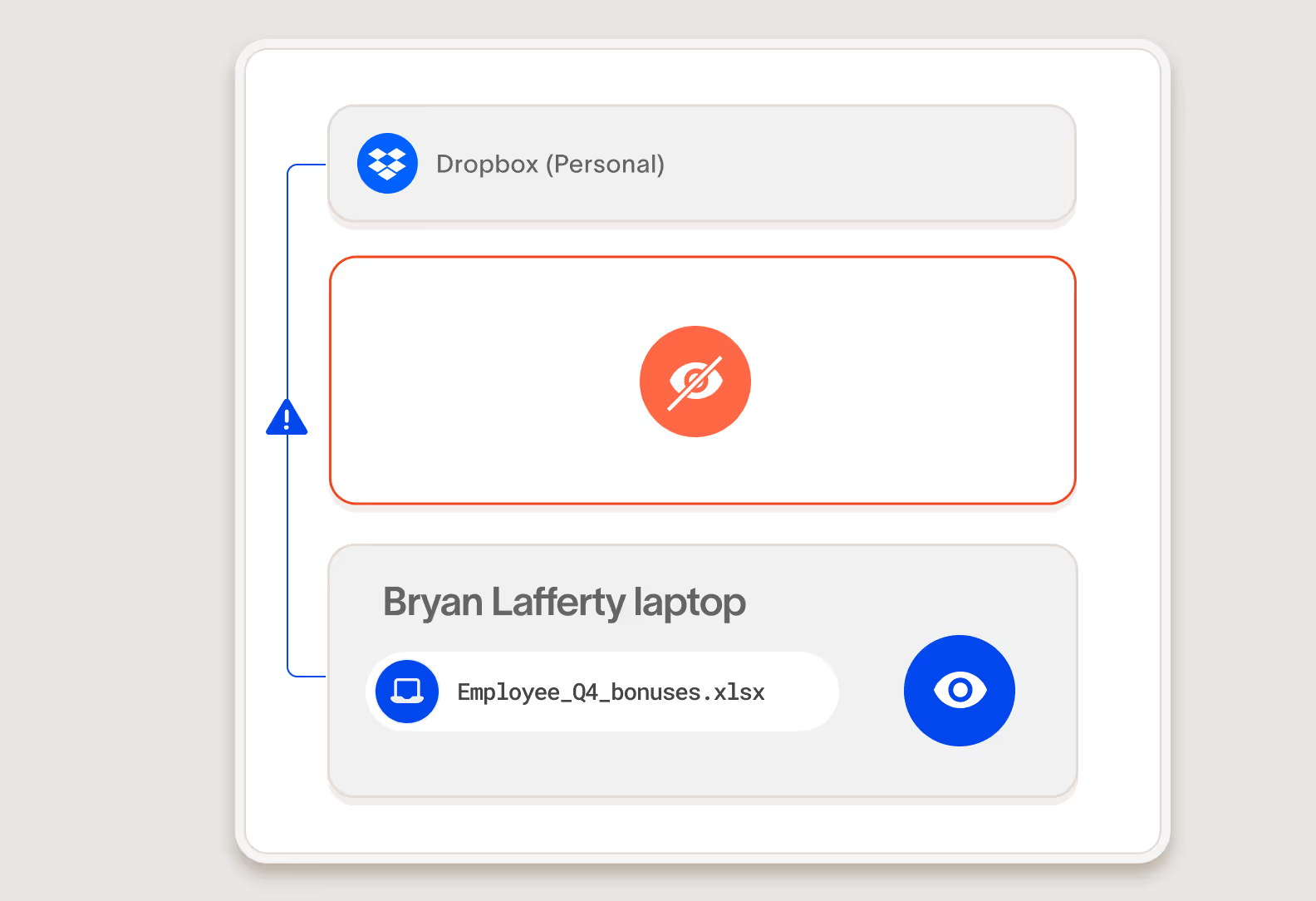
Proactively flag data vulnerabilities
Cyberhaven doesn't just find your data vulnerabilities—it pinpoints the ones that can actually be exploited. By using data lineage, we go beyond simple discovery and classification, showing you which risks truly matter.
The DSPM you know with the intelligence and execution you need
Uplevel your security posture by tapping into data context and applying controls to data at risk.
Advanced data discovery
Automate discovery of data and context, capturing risk factors such as access levels, identities, and movements. Correlate billions of data points to accurately analyze risks.
AI data classification
Leverage AI to automatically classify sensitive data both at rest and in motion without manual tuning. Improve accuracy, reduce overhead, and scale effortlessly across your environment.
Data lineage
Extend your understanding of data by revealing where it originated and how it's changed over time, helping you identify data risks more accurately than simple classification alone.
Data provenance
Accurately identify the origin of your data, categorizing it as Corporate, Personal, or Public. Provenance tagging helps you distinguish internal IP from external noise.
Microsoft Purview integration
Automatically read Microsoft Information Protection (MIP) and other third-party labels, unifying different classification schemas under one system of record.
Endpoint data-at-rest scanning
Inspect data stored on user devices, complementing cloud data discovery to provide complete visibility across endpoints and cloud repositories.
Unmanaged device detection
See every instance of sensitive data accessed from unmanaged devices, revealing both the data at risk and the user behind it.
Declarative Policies
Create data security policies based on a deeper understanding of data risk. Policies simultaneously protect data at rest and in motion.
AI data security
Enable safe generative AI adoption by automatically classifying sensitive data, tracking its movement, and enforcing policies when employees interact with AI tools.
Identity and access context
Flag data and data repositories with excessive permissions, ensuring that only trusted users have access to sensitive data.
Custom classification
Leverage natural language to define how your data is classified and address the unique challenges of your business and industry.
Cloud connectors
Easily onboard and connect to cloud repositories across your data estate.
Unified visibility and enforcement
Cyberhaven AI & data security platform
One unified solution for protecting data wherever it lives and goes.
DLP
Protect data and stop exfiltration: coach users and block leaks across email, web, cloud, and devices with reimagined Data Loss Prevention.
IRM
Combine data and behavior signals to stop insider threats, clarify intent, and catch slow-burning risks with Insider Risk Management.
AI Security
Increase AI adoption securely, understand shadow AI usage, assess AI risk posture, and prevent leaks without blocking teams with AI Security.






.avif)
.avif)
