Secure Data. Secure AI.
Cyberhaven’s AI & data security platform unifies DSPM, DLP, Insider Risk, and AI Security to protect data wherever it lives and goes across endpoints, cloud, on-prem, SaaS, and AI tools.
Cyberhaven AI & Data Security Platform
One unified solution for protecting data wherever it lives and goes
DSPM
Discover and classify data, detect risk as it flows between clouds and devices, and secure it automatically with Data Security Posture Management.
DLP
Protect data and stop exfiltration: coach users and block leaks across email, web, cloud, and devices with reimagined Data Loss Prevention.
IRM
Combine data and behavior signals to stop insider threats, clarify intent, and catch slow-burning risks with Insider Risk Management.
AI Security
Increase AI adoption securely, understand shadow AI usage, assess AI risk posture, and prevent leaks without blocking teams with AI Security.
Cyberhaven
solves your most difficult data security challenges
Today, data is fragmented: copied, pasted, captured in screenshots, embedded, and summarized. In the AI era, data has broken free.
Data sprawl increases costs and risks
Teams struggle to map sensitive data at rest and in motion, hindering regulatory compliance and driving up data retention costs.
Theft and leaks go undetected
Existing data loss prevention (DLP) tools are operationally complex and fail to prevent data exfiltration across modern endpoints and cloud services.
Risky insiders mishandle data
Organizations lack the necessary context and control to manage insider threats and accelerate their incident response effectively.
Shadow AI creates new risks
Limited visibility into shadow AI usage and AI agents makes it impossible to securely increase AI adoption or prevent new forms of data exfiltration.
In the AI era, your data has never been more valuable nor more difficult to protect. Organizations that harness their unique data will out-innovate their markets. Those who lose control of it will lose trust, revenue, and momentum.
More "workers" as AI agents create, transform, and move data at machine speed
of alerts from legacy data security tools are false positives
of data exfiltration involves fragments and snippets, not complete files
The chaotic reality of modern data sprawl
Why the data security landscape has changed with AI
Defined Perimeters and Pure-play Tools
A simpler time: discover, classify, and label files to enforce data movement.
Cloud, SaaS, & Real-time Collaboration
Democratized data broke the network perimeter, then the file perimeter, creating data fragments that evade controls.
The AI Era
AI tools democratize intelligence, creating exponentially more fragments, derivatives, and pathways for data.
Static defenses fail in a dynamic world
Why do existing data security approaches fall short?
No understanding of the data
“We realized our tools could detect patterns, but they had no understanding of what the data actually was, where it came from, or why it mattered.”
CISO, Global Enterprise
Unfit for how data moves today
“Our tools assumed data stayed whole. In reality, AI and collaboration tools shattered it into fragments that could no longer be labeled or tracked.”
VP of Security, SaaS Company
Hard to operationalize
“Our team spent more time tuning rules and explaining false positives to the business than reducing risk. The tooling created friction instead of clarity.”
Head of SecOps, Financial Services Firm
One platform for complete data control
Solving the AI & Data Security Problem
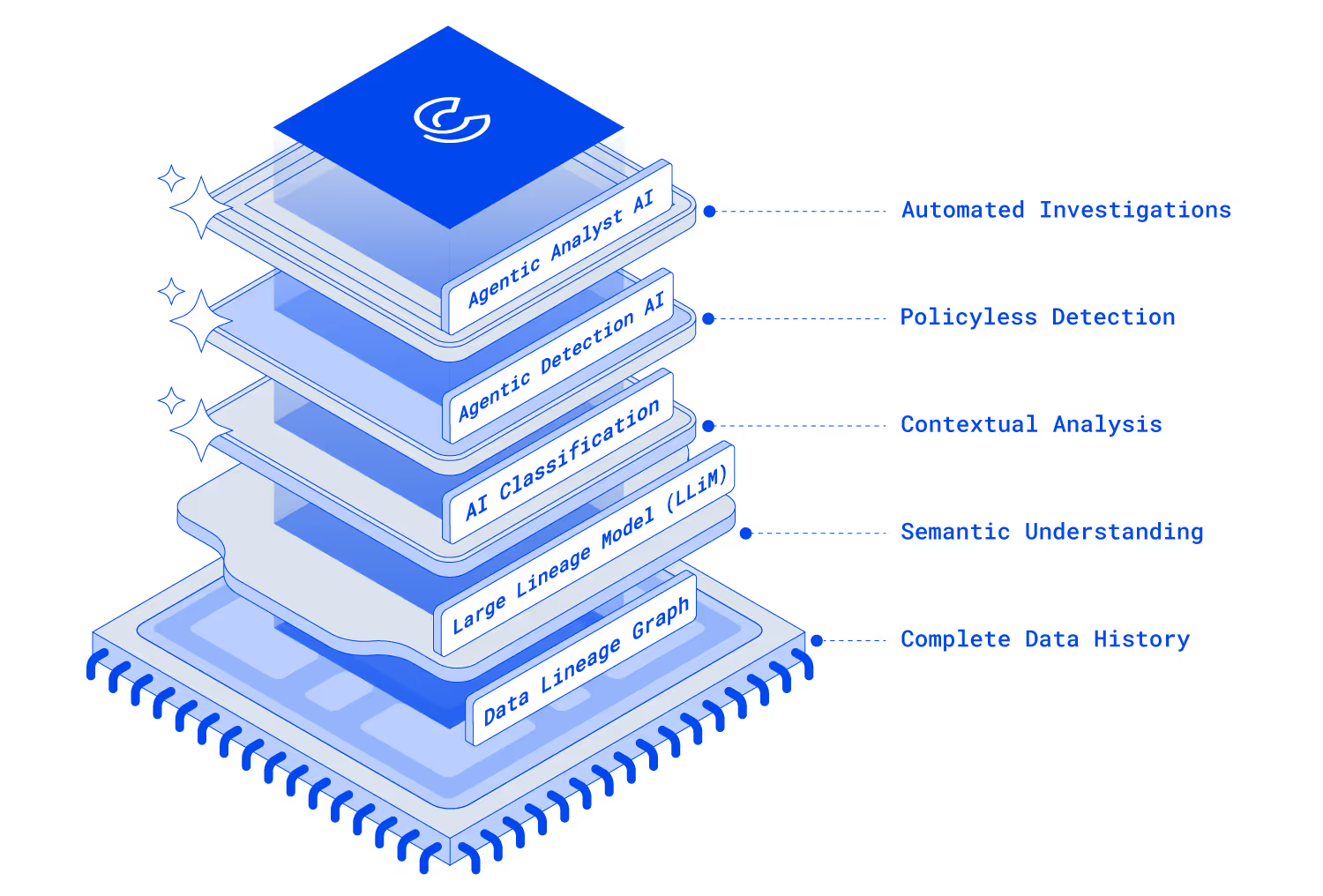
Deep Understanding
Trace end-to-end data lineage with context-aware AI classification to eliminate false positives and false negatives. Detect risk automatically with agentic AI and policyless protection.
.avif)
Holistic Visibility & Control
See where your data lives, how it moves, and who can access it across SaaS, cloud, endpoints, and hybrid environments with easy integrations, powerful visualizations, and contextual controls across every major exfiltration vector.
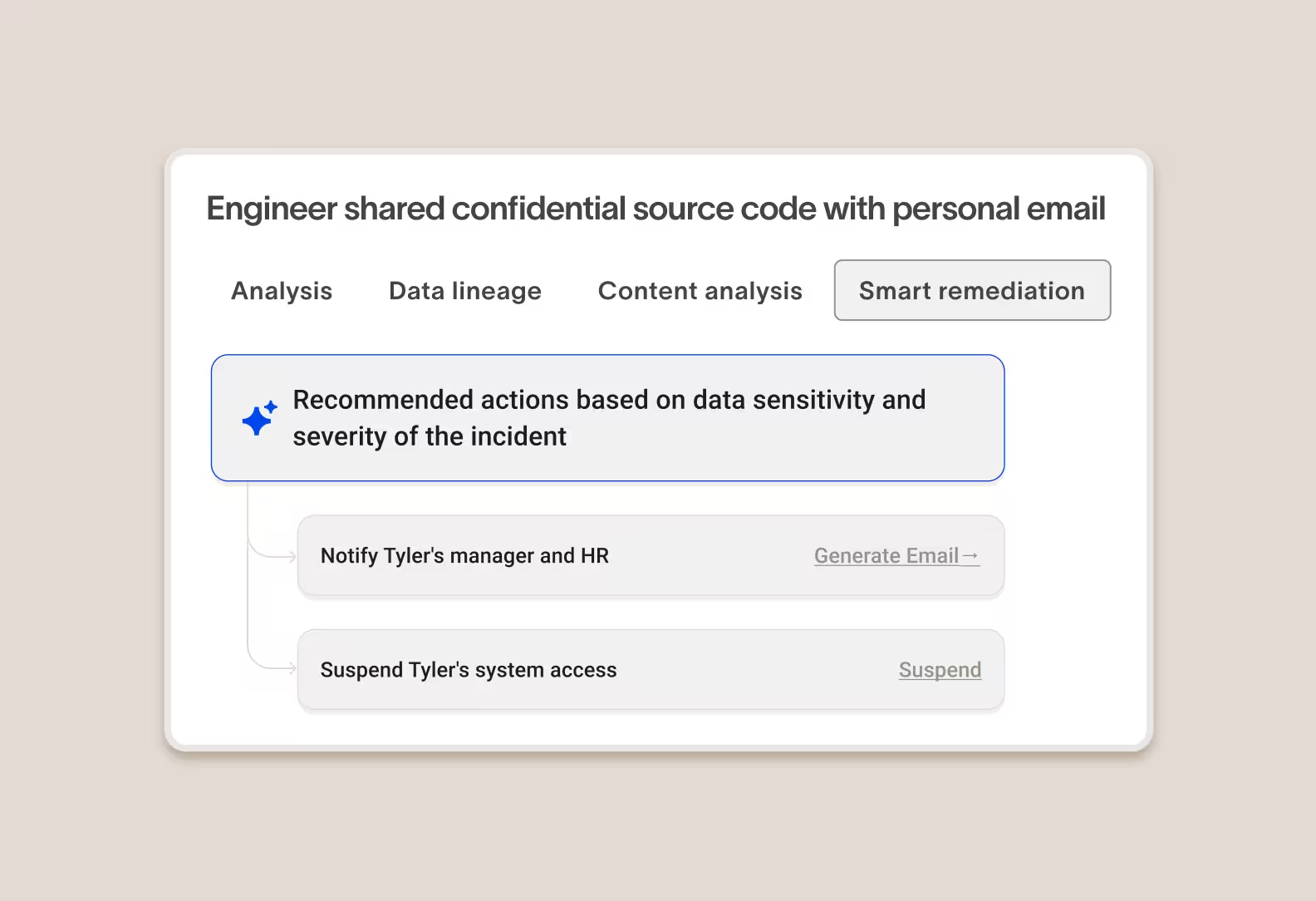
Easy to operate
Deploy fast, tune easily, and automate protection intelligently without disrupting users or security teams. Automatically launch investigations with agentic AI that delivers concise, comprehensive reports.
Solving the data risks that define modern work
How customers use Cyberhaven to secure their data
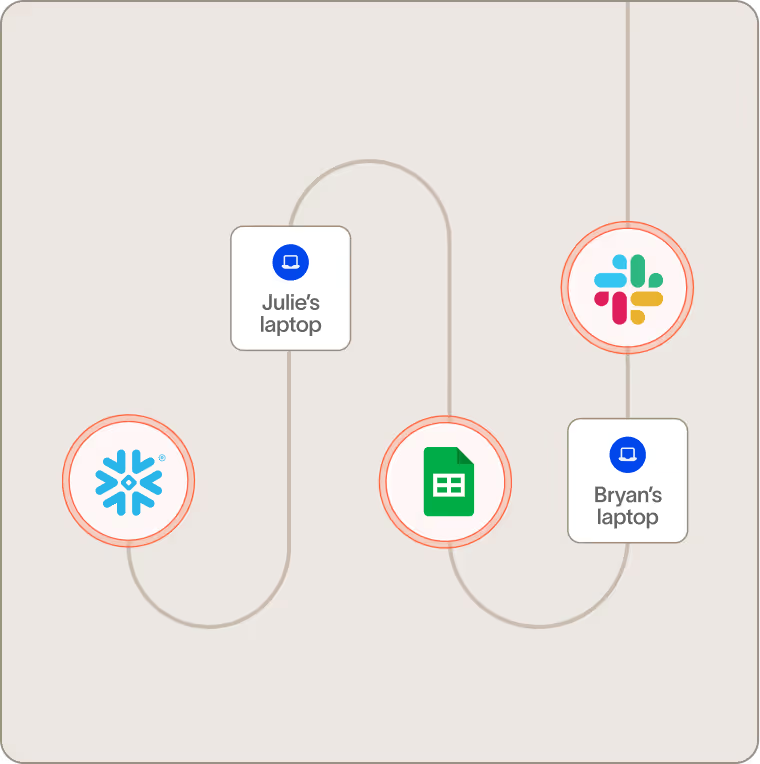
Discover and classify data
See what systems store different types of data and how data moves within your company. Trace every move across devices, SaaS, code repositories, shared drives, generative AI, messaging apps, and more.
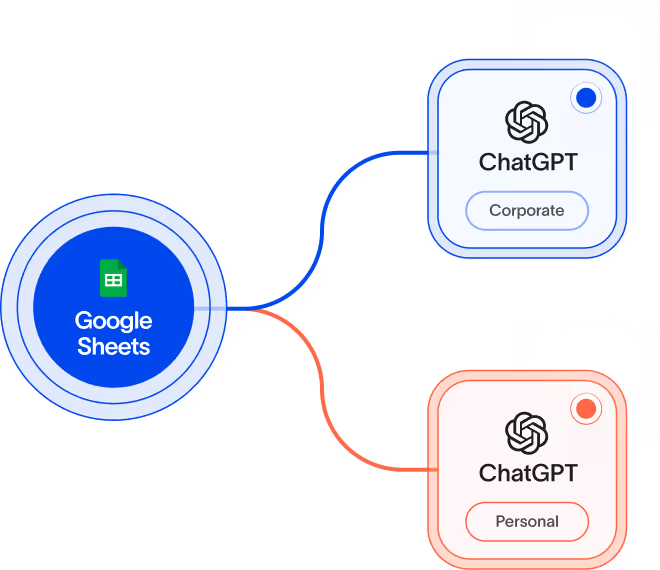
Securely use AI
Gain unprecedented visibility into generative AI with protection to match. Discover shadow AI, assess risk, and enforce controls so people work productively while sensitive data stays protected.
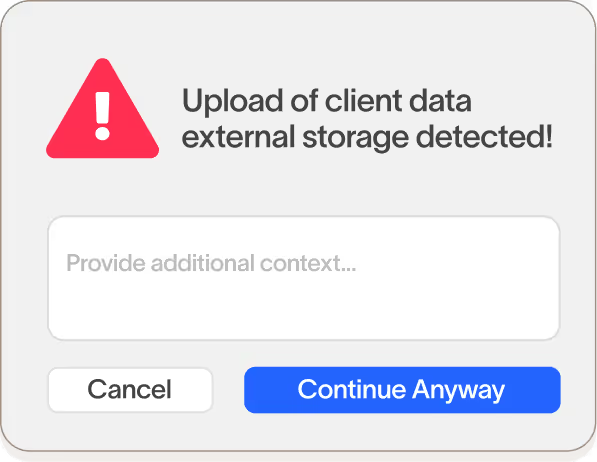
Detect and stop risky behavior
Instantly detect when a user handles important data in a risky way using Linea AI Detection Agent, stop them in real time, and coach them in the moment with contextual prompts that explain risks and reinforce policy.
.avif)
Accelerate internal investigations
Automate deep investigations. Cyberhaven’s Linea AI Analyst Agent launches investigations, analyzing screen activity, history, and data lineage in real time to deliver clear reports, so your team understands intent, has all the evidence, and can resolve incidents faster.
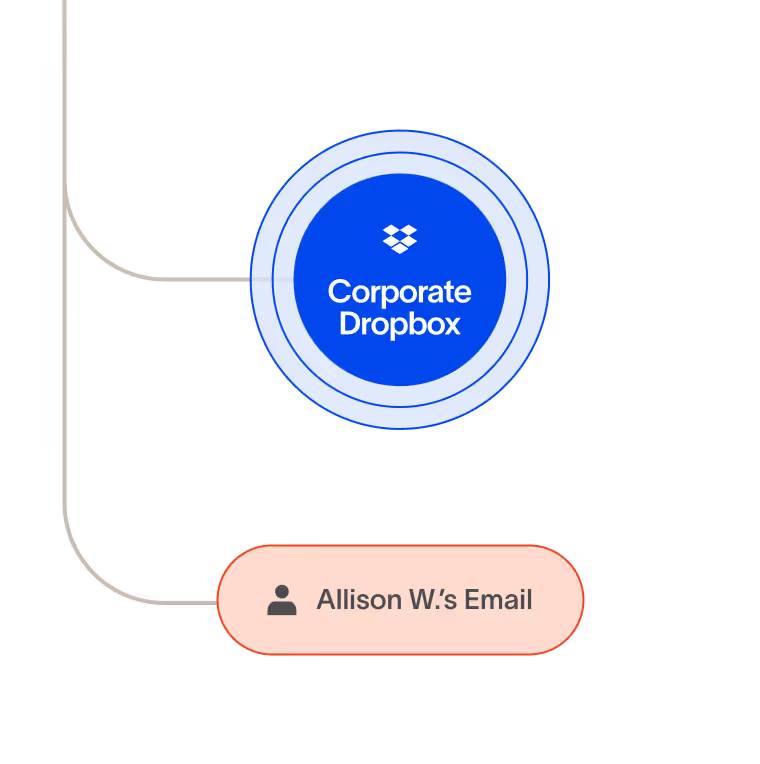
Strengthen compliance
Stay compliant without slowing down. Automatically classify data, track it in real time, and apply exact controls, with audit trails that prove adherence to GDPR, HIPAA, CCPA, PCI DSS, and more.
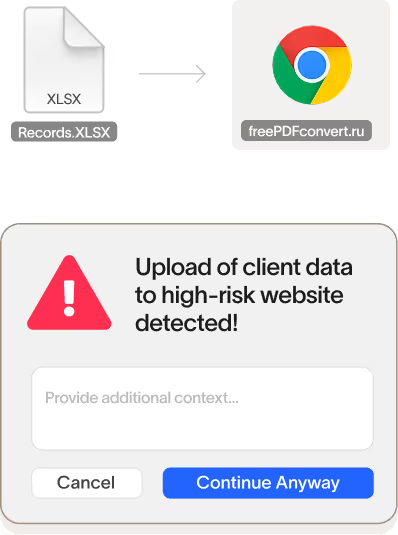
Stop data exfiltration anywhere
Use powerful AI-driven detection to block important data from leaving via web, email, removable storage, Bluetooth/AirDrop, desktop apps, generative AI, and more – without frustrating users or disrupting legitimate work.
Cyberhaven makes securing AI & data easier and more effective:
Faster Incident Investigation
Faster Incident Resolution
Fewer False Positives
Security that moves at business speed
Protect your data without slowing down your people
"Rolling out Cyberhaven was straightforward and efficient. Staff experienced no disruptions, and we quickly saw the benefits for our information management practices."
Gordon Burke, IT Project Manager, Mission Australia
"When you have a traditional system and you're just looking at all the blocked actions, there's just a lot of noise. [Data lineage] helps us identify things that you don't usually get to see with traditional DLP."
Mike Santos, Head of Security, Cooley
"I've used traditional DLP technologies in the past and sometimes the noise-to-signal ratio can be a lot. The context Cyberhaven gives us has significantly improved our data protection, monitoring of data movement, and insider risk."
Prabhath Karanth, VP of Security & Trust, Navan
"Staying ahead of the competition means guarding against insider threats. Cyberhaven gives us visibility into how data flows within our company and stops insider threats in real time."
Richard Rushing, CISO, Motorola
"Another nice feature of Cyberhaven is that you can tailor the response to the end users when they do something that triggers your policies."
Chris Payne, VP of Information Security, VaxCare
"Rolling out Cyberhaven was straightforward and efficient. Staff experienced no disruptions, and we quickly saw the benefits for our information management practices."
Gordon Burke, IT Project Manager, Mission Australia
"When you have a traditional system and you're just looking at all the blocked actions, there's just a lot of noise. [Data lineage] helps us identify things that you don't usually get to see with traditional DLP."
Mike Santos, Head of Security, Cooley
"I've used traditional DLP technologies in the past and sometimes the noise-to-signal ratio can be a lot. The context Cyberhaven gives us has significantly improved our data protection, monitoring of data movement, and insider risk."
Prabhath Karanth, VP of Security & Trust, Navan
"Staying ahead of the competition means guarding against insider threats. Cyberhaven gives us visibility into how data flows within our company and stops insider threats in real time."
Richard Rushing, CISO, Motorola
"Another nice feature of Cyberhaven is that you can tailor the response to the end users when they do something that triggers your policies."
Chris Payne, VP of Information Security, VaxCare
Advancing AI and data security together


.avif)








.avif)
.avif)
