One unified platform for AI & Data Security
Cyberhaven combines DSPM, DLP, IRM, and AI Security in one solution that’s more effective and easier to use than standalone tools.
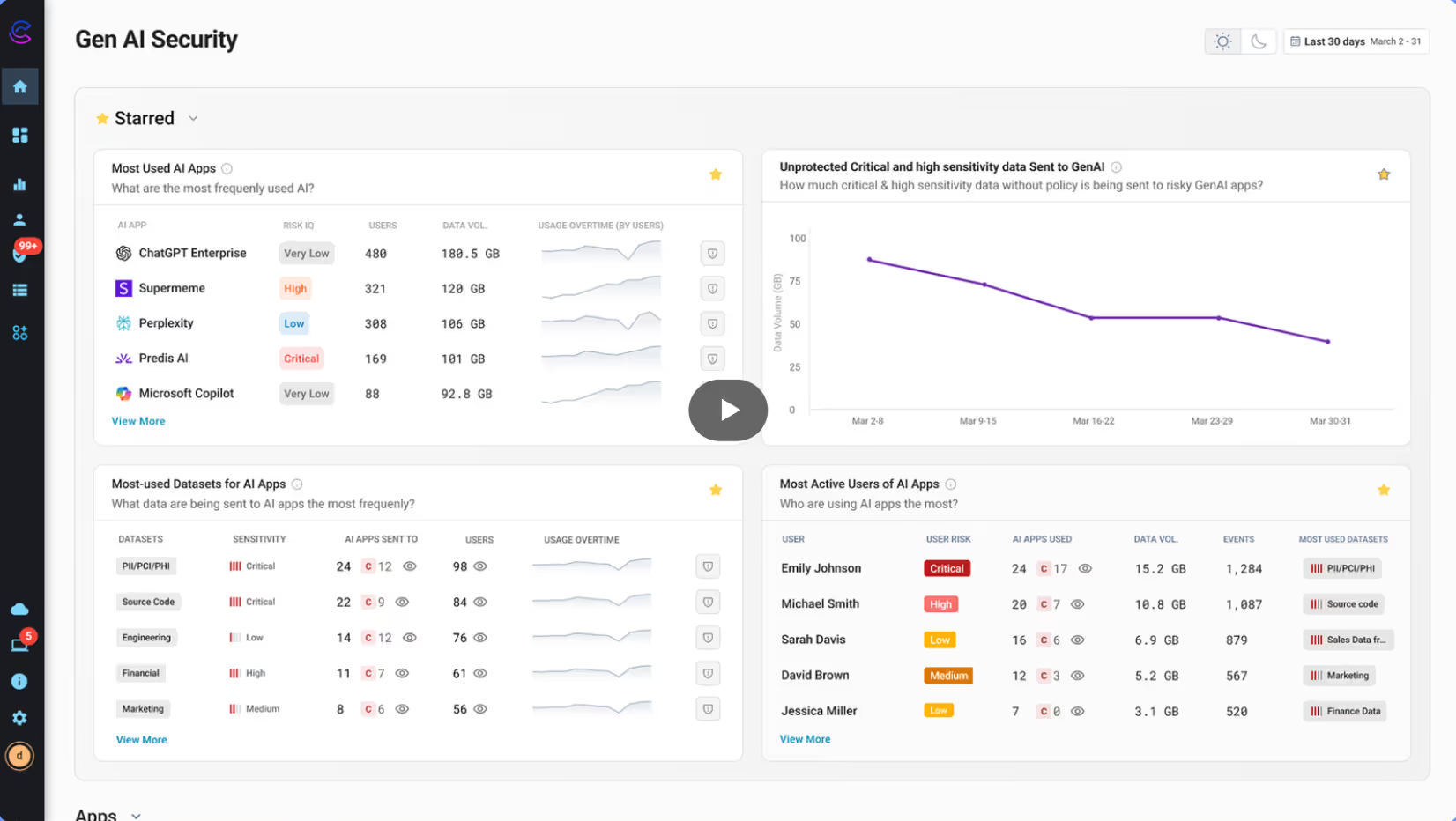
Cyberhaven AI & Data Security Platform
One unified solution for protecting data wherever it lives and goes
DSPM
Discover and classify data, detect risk as it flows between clouds and devices, and secure it automatically with Data Security Posture Management.
DLP
Protect data and stop exfiltration: coach users and block leaks across email, web, cloud, and devices with reimagined Data Loss Prevention.
IRM
Combine data and behavior signals to stop insider threats, clarify intent, and catch slow-burn risks with Insider Risk Management.
AI Security
Increase AI adoption securely, understand shadow AI usage, assess AI risk posture, and prevent leaks without blocking teams with AI Security.
Why Cyberhaven
Context is why Cyberhaven is smarter, easier, and more effective at protecting your data.
Our AI-native platform doesn't just inspect content: it traces its entire journey. See where data lives, comes from, how it changed, and who interacted with it. We’ve reimagined data security and insider threat with AI-powered automation and streamlined controls, so you finally get real protection that’s easy to manage.
Data lineage
Our data lineage technology maps the full journey of sensitive data, from creation to every movement, transformation, and fragmentation.
AI-based content intelligence
Cyberhaven uses AI to classify sensitive data the moment it’s created and continuously updates that classification as the data evolves.
Autonomous risk detection
Linea AI Detection Agent applies predictive AI using proprietary Large Lineage Models (LLiM) to instantly detect risky activity.
Accelerated investigations
Linea AI Analyst Agent launches deep investigations, gathers evidence, and delivers clear reports with next steps to resolve issues faster.
Return on investment
Finally, data security that’s easy to deploy and run
DSPM, DLP, and insider threat tools tools aren’t known for being easy to get up and running. Our approach is not only easier for administrators but better for end users too.
95% fewer false positive alerts
Compared with other tools, Cyberhaven not only improves detection of threats others miss, but reduces false positive alerts by 95%.
Simple, powerful policies
By layering in context in addition to content, Cyberhaven policies are easy to customize during initial setup and easier to maintain.
Modern cloud architecture
There are no servers or databases to manage, and Cyberhaven doesn’t slow down end user computers like some products do.
Integrations
Connect Cyberhaven to your
enterprise systems and SIEM








Enterprise-grade capabilities
When we set out to redefine data security, we included the standard features you expect.
Out-of-the-box policy templates
Get started quickly with dozens of out of the box policies for common use cases and industry-specific requirements.
Privacy and obfuscation
Ensures sensitive information displayed in the dashboard is obfuscated based on user roles, safeguarding data privacy.
Reporting and analytics
Includes out-of-the box dashboards and a fully customizable reporting engine for advanced analytics.
Role-based access control
Includes standard out-of-the-box roles or create your own custom roles with any combination of permissions.
User directory support
Integrates with on-premises and cloud-based directory services to support granular user group and department based policies.
Built on open APIs
Natively integrates to SIEM tools and exposes incidents through an API so you can add them to any third-party security tool.
Tamper protection
Equips the endpoint agent with robust hardening measures, preventing tampering by malicious end users.
Platform security
Our cloud platform is fortified with industry-leading security standards, ensuring your data and operations remain protected.
One unified solution
Consolidate tools and vendors
Combines multiple solutions in one experience that outperforms in each standalone category.
One policy that applies everywhere
Apply standardized policies wherever data goes and simplify management.
More effective than the sum of its parts
Correlate user behavior and data awareness to focus on risks that actually matter.







.avif)
.avif)
