←
Back to Blog
Security best practices
3/12/2025
-
XX
Minute Read
The file and SaaS data perimeter is broken: data security needs data lineage
We are in the midst of a major technological shift. And when shifts happen, new industry-defining companies emerge. The winners aren’t just those with great ideas—they are the ones who adapt and respond to change the fastest.
I witnessed this firsthand. Back in the mid-2000s, when the security world revolved around networks and endpoints, I spent nearly a decade at Symantec. Then cloud, SaaS, and APIs started reshaping everything. I remember pitching to executives about investing in these new technologies. They didn’t. So I left and built CirroSecure, which ultimately became Palo Alto Networks’ Prisma SaaS platform.
Palo Alto Networks and CrowdStrike thrived because they understood context better than anyone else. Palo Alto redefined network security by identifying applications and users in ways no other vendor could. CrowdStrike revolutionized endpoint security by mining massive datasets to detect threats others missed. Their success was rooted in one thing—understanding the flow of data.
The next paradigm shift: AI & data
Today, we are entering another seismic shift—this time driven by AI. And AI is all about data. This puts Cyberhaven in a unique position to empower our customers in this new era.
Let’s take a step back and consider how we consume data today.
The broken data perimeter
A decade ago, our data perimeter was well-defined: files and SaaS applications. Enterprises built security solutions around this structure—classifying and labeling files, monitoring emails, and setting policies based on file movement.

But today, that perimeter is shattered.
Data is no longer confined to structured files within SaaS applications. Instead, it's highly fragmented and derivative—spreading across an organization in new ways.
Consider this:
- A few years ago, a SalesOps team member would check Salesforce for customer ARR.
- Today, they simply ask a Slack bot, which pulls data from Salesforce and other sources.
- The result? Knowledge fragments are scattered across platforms, detached from their original context.

This isn’t just a workplace phenomenon. We consume news the same way—tweets, blogs, articles—all blended together. To verify authenticity, we trace the source. That’s lineage.
Why data lineage is the future of security
In a world where data is fragmented and constantly transformed, lineage isn’t just a feature—it’s a necessity for data security.
Today, we still live in a user-driven data consumption world. But as Agentic AI takes over, data consumption will shift to system-driven, where AI synthesizes and generates entirely new outputs.
Without lineage, data protection fails
Any company that does not have data lineage will struggle to secure sensitive information. Cyberhaven has spent years perfecting Data Lineage, enabling organizations to:
- Accurately classify data: If a piece of data—or its derivative—originated in Salesforce, we know it might contain sensitive sales information.
- Resolve incidents faster: Lineage enables analysts to connect the dots, tracing the data journey in seconds.
- Understand enterprise data flows: Lineage reveals how data moves across an organization, allowing security teams to craft smarter policies.
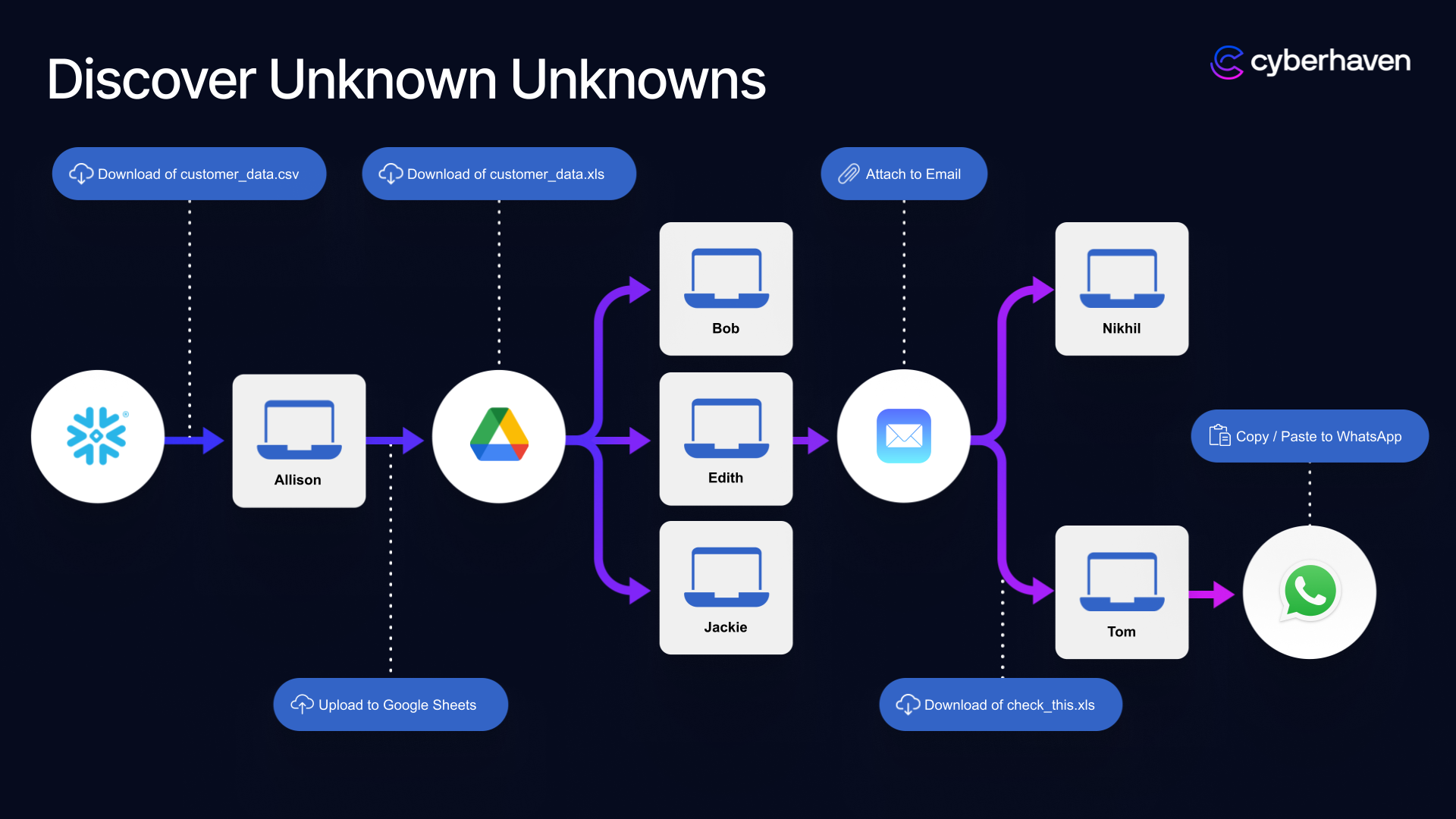
Not all lineage is created equal
For lineage to be effective, it must meet three critical imperatives:
- Comprehensive Tracking – True data lineage must capture how data flows across all endpoints, covering its full lifecycle.
- Derivative Awareness – Tracking must include copy-paste, screenshots, renames, and all other transformations of data.
- Real-Time Querying – Lineage must be instantly searchable—in milliseconds—to determine whether a data action should be blocked.
Cyberhaven was built with these imperatives in mind. This is why leading companies trust us to protect their most valuable asset—their data.

