←
Back to Blog
Security best practices
7/15/2024
-
XX
Minute Read
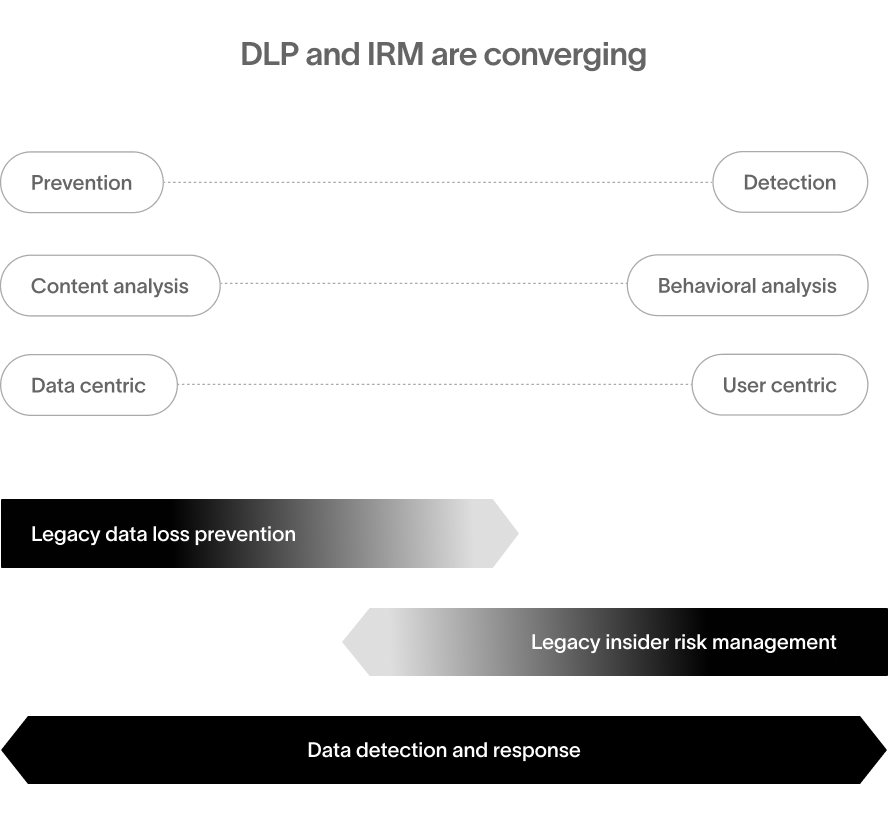
Modern data security: why the convergence of DLP and IRM is more effective than the sum of its parts
In the past decade, organizations seeking to protect sensitive data from negligent or malicious insiders faced two choices: invest in a Data Loss Prevention (DLP) product or an Insider Risk Management (IRM) product. These solutions addressed the same problem from different angles. DLP products focused on analyzing data content to control its movement, while IRM products monitored user behavior for risky actions.
Today, the landscape of data security is changing. A new generation of data security products is merging the capabilities of DLP and IRM into a single solution. Meanwhile, legacy vendors are incorporating features traditionally found in the other category into their products. This convergence goes beyond tool consolidation; it combines data and user behavior analysis for more effective data protection.
“Gartner sees that DLP vendors are increasingly converging with insider risk management platforms. This convergence enables better detection of data exfiltration as it enriches DLP events with anomalous user behaviors, improved risk scoring and real- time monitoring capabilities.”
- Gartner, 2023 Market Guide for Data Loss Prevention
{{ promo }}
Understanding data loss prevention
The strength of DLP technology lies in its ability to analyze the content of the data and take action to control its movement.
Key aspects of DLP include:
- Analyzes content: DLP tools inspect data for specific patterns that match predefined sensitive criteria, such as credit card numbers, Social Security numbers, or part numbers.
- Prevents data from leaving: Upon detecting these patterns, DLP products can take immediate actions like blocking uploads or preventing messages from being sent.
- Data-centric approach: DLP technology prioritizes the control of data movement, regardless of the user handling it.
Understanding insider risk management
Insider Risk Management (IRM) tools, sometimes referred to as UEBA, focus on identifying and alerting organizations to behavior that indicates a potential insider threat.
Key aspects of IRM include:
- Analyzes behavior: IRM platforms analyze access frequency, data movement volume, and communication habits to detect deviations from typical user behavior.
- Alerts security team to investigate: IRM tools aim to provide early warnings of potential security incidents, but they generally do not take action by themselves.
- User-centric approach: IRM technology focuses on the actions and behaviors of individuals within the organization without necessarily understanding the type of data they are handling.
Combining traditional DLP and IRM signals
As DLP and IRM vendors add features traditionally found in the other category, they not only meet customer demand for tool consolidation but also enhance data security against insider threats.
Improved risk detection
Combining content analysis with behavior analysis can flag incidents that would otherwise not appear in isolation to be a serious risk.
Example: A user downloads a spreadsheet containing employee Social Security numbers, compresses it in a ZIP container to obscure its content, then copies it to a USB storage device.
A DLP tool would see a spreadsheet containing hundreds of numbers matching a Social Security number pattern along with the word “SSN” but would lose insight into the content once it is compressed. An IRM tool would see a user compressing a file in a ZIP container then renaming the file before transferring it to a USB drive without knowing the contents. But together, we can see that the user is compressing sensitive data and it appears they are attempting to obfuscate their behavior, which is a critical risk.
.png)
Reduced false positives
Similarly, correlating information about the content and behavior can reduce false positives that would otherwise be detected as a risk with a narrower picture of events.
Example: A user uploads a large volume of data comprised of video files from the recent company picnic to their personal Dropbox from a work computer.
A DLP tool would see that the data does not contain any sensitive content patterns. But an IRM tool without visibility into the content would detect this as a serious risk because of the volume of information being transferred is anomalous and could signal a threat. Together, we would be able to see that while the volume of data is anomalous, it is likely not sensitive.
.png)
Data detection and response: a new approach built natively with DLP and IRM
Legacy DLP and IRM vendors are adding capabilities traditionally found in their respective offerings. At the same time, a new generation of data security products is coming to market that combines the best of these legacy product categories and builds on them to more effectively protect data. Data Detection and Response (DDR) solutions go beyond the traditional DLP and IRM feature sets, leveraging these capabilities in novel ways.
Classifying data using events not just content
Relying solely on content inspection to identify sensitive data makes it challenging to classify data without consistent content patterns (e.g., customer documents, design files) or no text (e.g., recorded meetings, pre-launch marketing images). DDR uses event context to classify such data.
Events combined in a data lineage provide more insights into the type of data:
- Where it originated: Specific types of data originate from specific places (e.g., customer databases in Snowflake, source code repositories in GitHub).
- How it was handled: Data moves through recognizable channels (e.g., SharePoint for board meetings, Google Drive for client documents).
- Who added to it: Different employees produce different work (e.g., researchers developing drug formulas, designers working on new products).
Tracking risky data ingress
New employees might bring confidential data from previous employers, and AI-generated content can include copyrighted material or malicious code. DDR traces the lineage of all data, allowing detection of potentially sensitive material entering the environment.
Recording all events for investigations and policy back-testing
It is common practice to monitor employees who have given notice or triggered other watchlist criteria closely. DDR supports these workflows by capturing and visualizing all data an employee interacted with during their tenure. This historical data allows for back-testing new policies to see their potential impact.


